Following on from my last post we had a GUID starting C1CDD (normally I would write the whole GUID down, but for the sake of not boring you all, I will keep it short), in this post we are going to see how that is useful.
Starting inside the Software Hive and finding the following key (Zelda style)
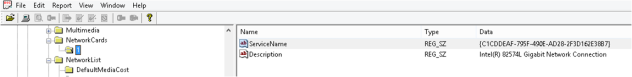
SOFTWARE\Microsoft\Windows NT\CurrentVersion\NetworkCards
As you can see from the massive list of network cards (you will most likely have more than one, depending on where the machine has been used) key ‘1’ contains the C1DCC GUID from earlier. You can now associate that with the Intel 82574L NIC. This will be useful to prove it was the actual NIC in the machine and not a VM (or vice versa)
Next Zelda, I need you to find the following Key
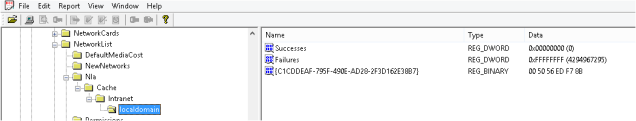
SOFTWARE\Microsoft\Windows NT\CurrentVersion\NetworkList\Nla\Cache\Intranet
Under Cache you may also have ‘Wireless’, but as no wireless card is configured with this VM, we don’t have one here. Under Intranet you will see a list of domains that your machine has been connected to. ‘localdomain’ is the same domain as the previous post shows us (go see for yourself) and there is that magical C1CDD again. This time pointing at the MAC Address of the default gateway of the ‘localdomain’ network.
Next my Robin Hood/Yellow Haired Elf Hybrid we need to find this Key
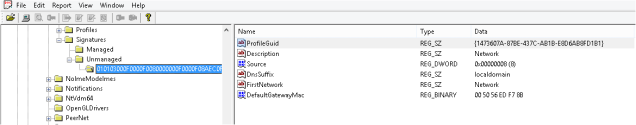
SOFTWARE\Microsoft\Windows NT\CurrentVersion\NetworkList\Signatures\Unmanaged
This part can be a little annoying if unlike me you have multiple entries in here, click through until you get a match of ‘DefaultGatewayMac’ with the MAC address from the previous step (you are making notes of all these and where you got them from…. right?). If you know of another way of finding this please leave a comment below, everyday is a school day after all.
Now make a note of the ‘ProfileGuid’
And now young Zelda, for the final Key, not technically the Boss Key, but still…
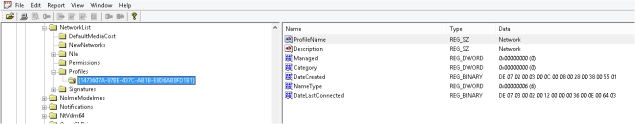
SOFTWARE\Microsoft\Windows NT\CurrentVersion\NetworkList\Profiles
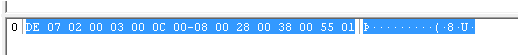
Under the Profiles key you will see the ProfileGuid as a key name. This Key holds the data regarding the first and last time the network was connected to. Both of these date stamps are in 128 bit System time, which I will go through decoding in a moment. Firstly you will notice the ‘ProfileName’ does not match the ‘localdomain’, this is due to it being a cabled network, a Wireless network gives the name of the SSID here as well as under ‘Description’, the way you confirm this is a wired network is from the ‘NameType’ field, here is a short list of possible options you will meet:
- 0x47 = Wireless
- 0x06 = Wired
- 0x17 = 3g
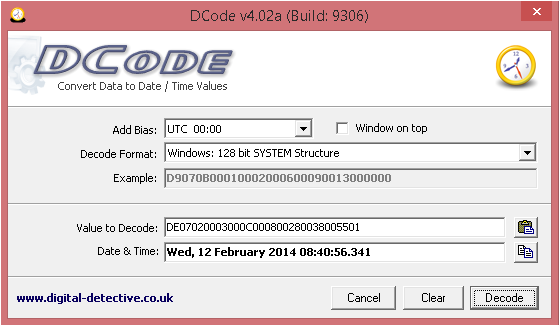
In order to decode the 128 bit system time you will need to use
Dcode Date can decode a variety of times from Windows (except Microsoft seconds, no one can figure those things out, luckily we aren’t installing anything)
Highlight the Hex from the bottom right window, then either CTRL+H or right click -> Copy Hex and paste it into DCode Date, ensure ‘Windows 128 bit SYSTEM structure’ is selected from the drop down and hit Decode. You should see the outcome as below: