Having all this information is all well and good, but right now all we can say for sure is that a USB device was used on this machine. Just because someone logged on to that machine doesn’t make them the target of the investigation. As forensic investigators we need to ensure that all of the links in the chain are connected. We need to prove User X used USB Device Y in Machine Z (we also need to say when it happened, but that’s for part 7!)
What do we know so far?
- 2x Devices are relevant to this investigation
- A ‘generic’ USB device was attached
- named “FOR408-USB”
- with a serial Number of 92B0564
- A Seagate USB Hard Drive was also attached
- named “My Drive”
- with a serial number of 2GE4D91T
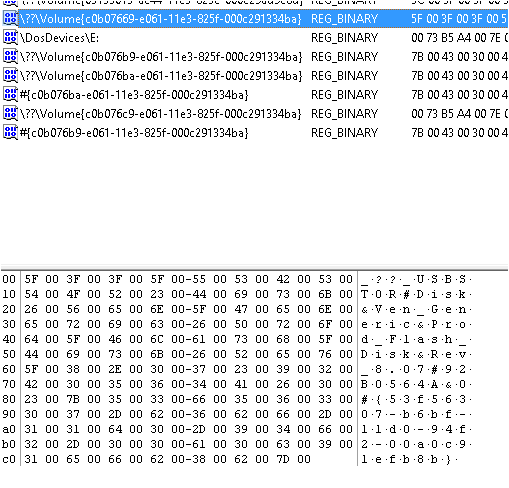
In order to find which user had these devices plugged in, we need the GUID. This can be found under the previously seen key:
SYSTEM\MountedDevices
From this previous screen capture we can see the Generic USB device highlighted. After \??\Volume you can see there is a string. This string is in fact the GUID of the device, make a note, you will need this later.
As you may recall, we could not find the key entry for the USB Hard Disk at this stage, the GUID for that device is actually remarkably hard to find (this could well be due to knowledge limitations, however I shall not be beaten). Should the investigation into the USB devices be stopped here? Nay! To the Nay sayers, I say Nay!
I will start off with the easy win. The USB Flash drive known as FOR408-USB. The GUID for this device is:
C0B07669-E061-11EF-825F-000C291334BA
Now we move onto the NTUser.dat, if you have lots and lots of users…. you have my sympathy, just kidding, try Grep see if that works, if not…. read previous statement.
I however have a strong suspicion that this one user (me) is the target of this investigation, how do I know? Simple. I told me.
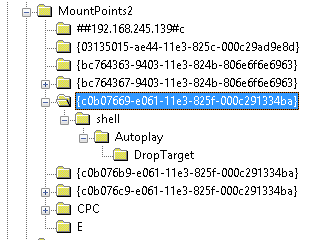
So I open the NTUser.dat file and browse to the following key
NTUser.dat\Software\Microsoft\Windows\CurrentVersion\Explorer\Mountpoints2
As you can see the GUID matches, proving this device was used by this user!
What about the other device?
So this annoyed me a little, I know the other device was used by this user, so I wanted to be able to prove it. I manually looked through the other GUIDs in the list to see if there were any tells. Luckily for me, there was!
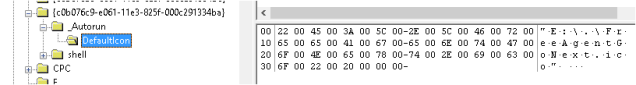
It turns out my USB Hard Disk has vanity issues and likes to carry around it’s own icon! This is far from forensically sound, but it does make me think this is the same device. I test the theory by plugging the device in to see if this file (e:\FreeAgentGoNext.ico) exists:
And it does! So I figured that the GUID shown has a good chance of being the USB Hard Disk:
C0B076C9-E061-11E3-825F-000C291334BA
I did a search in the SYSTEM hive for this string and found it in the Mounted Devices section
Still not 100% proof, but certainly proves that a device with the same GUID, as a device which holds an icon file, with an identical name to the Seagate drive, was plugged into that machine.
It may be a coincidence but the Hex value for this GUID is also the same Hex value for the E: drive letter in the Mounted Devices key (0073B5A4007E000000000000) possibly showing that the USB Hard Disk was the last device to be associated with the drive letter E:
Adding to that the NTUser.dat reference to E:\FreeAgentGoNext.ico certainly reinforces that theory.
Final thoughts
I will admit there was a fair amount of luck involved with finding the GUID for the “My Drive” device, and it’s not 100% proof. But I believe that if you can convince a non-biased technical person that this device was plugged into that machine using only the evidence above, then you have a good enough case to attempt to convince a jury. As previously stated, make a note and move on.