Often when analysing attacks, scans or just general traffic it is difficult to identify the specific tool or technique in use. This is simply because there isn’t a reference database for every tool.
So I thought I would upload a nice simple PCAP of OpenDoor Scanner so that if this is being used against you, you have the possibility of spotting it.
Quick disclaimer: this was used with no options, arguments or exclusions. This is the tool used with the default command line:
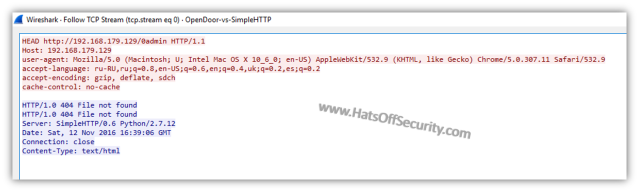
"python ./opendoor.py --url "http://privateIPaddress/"
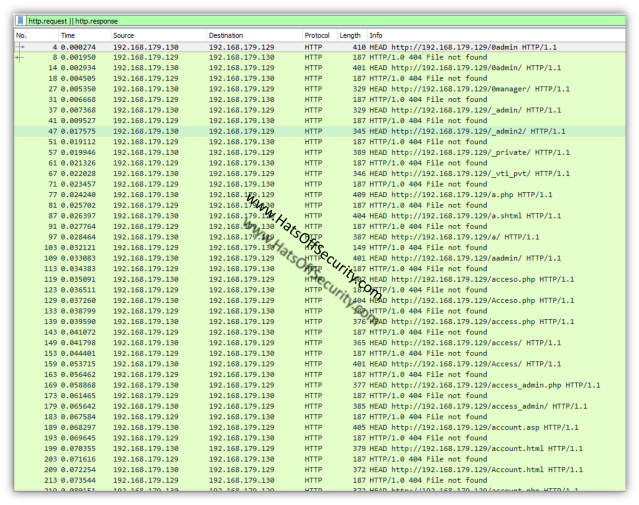
One of the first things to note about this tool is that by default it only does “HEAD” requests. This only requests the header from that specific page and not the body (i.e. no data from the page; images, text etc). It also runs alphabetically, which is not uncommon, but certainly helps easily identify a scan.
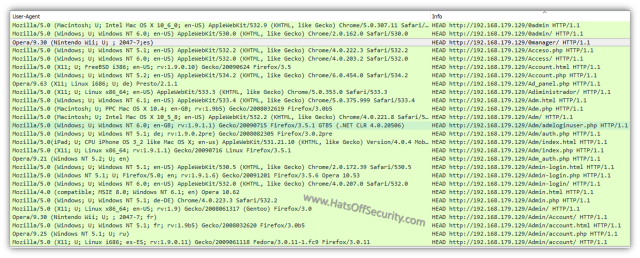
The User-Agent field changes, in fact it does not appear to be the same for any two requests. This may be an attempt to avoid automatic blocking, or maybe just the author was a little bored 🙂
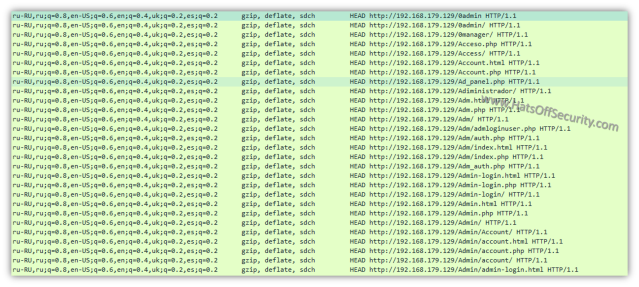
The ‘accept-language’ and ‘accept-encoding’ fields remain the same throughout. This is probably one of the best identifiers.
Analysing the PCAP
In order to see if you were affected by this I recommend the following filter in Wireshark:
http.request || http.response
This will show all requests (GET, HEAD etc) and all responses (404, 302 etc). You are looking for anything that is not a ‘404 not found’ response.
200 OK – Generally what the attacker is looking for, this means a page was delivered. Bear in mind however, some devices show a custom 404 page, meaning a 200 response is shown, but it is not the page the attacker wants.
30x – Typically a 302, however could be 301, 303 or 307. This will be in place if the page has moved, but may also redirect to a HTTPS version of the page. Watch what the responses are and work with the web dev team to decide if any action needs to be taken. I have seen a 302 give an IP of the internal interface of the webpage. While this isn’t a critical failure, it’s not good.
403/404 – Unauthorised and Not Found respectively. 404 is by far the better option. 403 gives the attacker hope the page is up, but not available to them right now. They may try to pivot back at a later attack stage.
418 – I’m a Teapot. If your server responds with this; either your web dev team have a sense of humour or you’re already screwed 🙂
I hope this helped. Please leave a comment with any constructive feedback and pop back anytime!

There has an updated version of Opendoor. Please try to compare new