I recently created a cloud based virtual machine, the purpose of this will be for an HTTP honeypot, but I thought first off I would leave it for a few days to see what happened. This VM has only port 22 open and the IP has not been published anywhere.
Within 30 minutes the brute force attacks had started!
I decided to keep an eye on what usernames were being used and realised that a lot of people are still setting up their systems with ‘root’ or ‘admin’
Even if your password, or key, are super secure and you are 100% confident they will never be guessed/cracked, there is still logic in creating weird and wonderful usernames. Mine for example is made up of items I saw on my desk, I then saved that username to LastPass for reference.
What logic you ask? Well let me create a scenario….
You create a server and have root as the only user (silly person). You give it a 32 character random password and sit happily in the knowledge it can’t be brute-forced. You then look at your auth log and see several thousand attempted root logins per day, as per below (screenshot after 48 hours). Two questions:
- Are you under attack?
- Yes.
- Are you under a targeted attack?
- No idea!
Now let’s keep the same scenario except the username has now been changed from ‘root’ to ‘HOS_Desk_Envelope’, this makes creating an alert so much easier. With only a single failed instance you can say that someone has a higher level of knowledge than they should about your build. Have you had an OpSec leak? Is your username on Pastebin? Or did a staff member simply type an incorrect password. Let’s go back to our questions:
- Are you under attack?
- Yes.
- Are you under a targeted attack?
- No.
Such a simple change provides such a huge benefit. No one, company or individual, should be using generic usernames in internet/production systems.
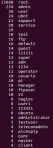
For reference, here are the top 50 usernames along with how many times they were tried in a 48 hour period on a server that isn’t advertised anywhere.
15719 root
254 admin
36 user
24 ubnt
21 support
20 service
18 test
16 ftp
16 default
14 guest
14 111111
13 super
13 adm
13 1234
11 operator
10 usuario
10 pi
10 manager
10 ftpuser
10 22
9 nagios
8 user1
7 123321
6 ubuntu
6 administrator
5 testuser
4 telecomadmin
4 plcmspip
4 osmc
4 master
4 client
3 sysadmin
3 git
3 elastic
3 0101
2 zabbix
2 uucp
2 tomcat
2 sysadm
2 supervisor
2 student
2 steam
2 sinusbot
2 scan
2 raspberry
2 postgres
2 PlcmSpIp
2 oracle
2 Operator
2 mysql