Continuing on from yesterday’s post regarding Hive files not updating:
A colleague and I (say hi Joe) have been doing some research on this along with some very helpful comments from Brian Moran (@brianjmoran) via Twitter.
My previous post commented that Hives were not updated on the fly. The main reasons for this conclusion were the following:
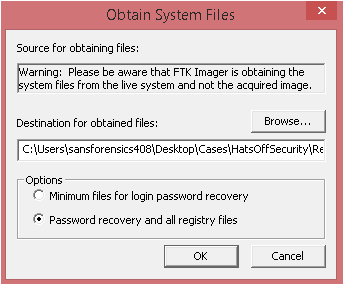
- After installing a USB device then using FTKImagers capture locked files, the System hive still did not show the USBStor Key
- This above process was repeated with variations, however the common factor was using FTKImager capture locked files
- The modified timestamps on the Hives were a few days old, leading me to believe they had not been modified
- The last reboot time extracted from the registry (I will make a post on how to do this another time) matched the last modified time of the Hives
- The same timestamp anomaly was present on other Windows 8 machine (my wife’s laptop)
- This behaviour did not match previous versions of Windows (timestamps or FTKImager locked files)
All of these points led me to the belief that Windows 8 held the Registry in a cache somewhere and wrote it to disk on shut down/restart. This seemed like a very important point due to how a lot of DFIR teams capture ‘fast forensic’ data. It was also very easy to become focussed on the timestamp of the file. The fact that the tool (or feature of the tool) that I was using was not working as intended and instead was showing what I wanted to see meant that I placed too much faith into it. Please don’t take this as a sign of FTKImager capture locked files as being broken, I don’t know why that happened, but it proves that you must always double check.
Just to show it wasn’t as easy to spot using only one tool, below are the two System Hives, the top one has no USBStor key and is an old version, the bottom is the working Hive with USBStor.
and below is the FTKImager capture locked files screen which warns you that these are being captured from the live system
The comment left by Brian suggests this post regarding Windows 7 is most likely what is the cause (although this link is referring to Windows 7 the Hives in W7 do update the timestamps, as such this is still a Windows 8 ism)
Allow me to also take you through the process of the Hive files are updated. (If this isn’t in order, it’s because I didn’t make notes!!! I can feel Chad Tilbury giving me daggers already….)
First off, add the logical drive in FTKImager as an evidence item (still a good tool after all), browse to %system32%\config and right click the Hive to extract. I am sticking to the System Hive as I know the USBStor isn’t in the original, but it in the live Registry.
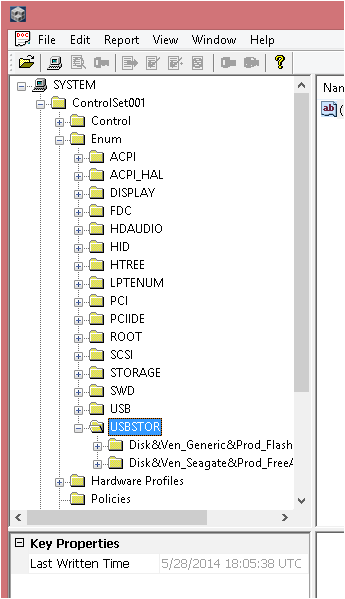
Opening the manually extracted Hive and opening with Registry Viewer we can see:
Make a note of the ‘Last Written Time’, as you can see this is not the same as the modified time of the Hive.
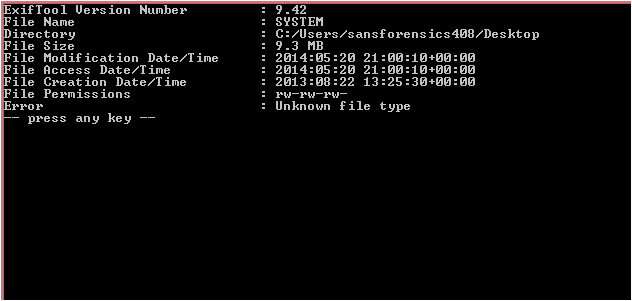
And to prove the meta data I ran Exif Tool against the above Hive and got these results (Exif tool was not really designed for Hives, it looks for meta data, however I just wanted to show the modified time in another way other than Windows Explorer)
And yes it is on the Desktop, not best practice I know. Also to explain the username, this VM is the Windows 8 SIFT workstation as provided when attending SANS courses. I strongly recommend the 408, just because it starts with a 4 don’t under estimate the knowledge you can gain from it.
Conclusion
My biggest take away from this whole exercise is to remember there is more than one way to look at the data, I actually intentionally missed a few steps from here that Joe and I went through today, including creating user accounts and checking the SAM Hive, running system maintenance and learning that updates the contents of the RegBack folder. I didn’t feel these would add anything to this post. Unless you want to see how to search through Hex in FTKImager using Ctrl+F.
I also realised how good the SIFT Workstation is; the machines I tested this on were host Windows 8 boxes with a basic install, finding the tools needed proved to be almost as annoying as looking at the problem!
And conclusion for the Hives? The timestamps can’t be trusted, as Brian quite rightly points out in his comment. I do not currently know what causes the timestamps to update, I know it happens on a reboot, but how/why? Would a hard reboot (pulling the power) corrupt the registry? Unlikely as we have seen the registry is written to, just not finalised. Perhaps the fact the Hive was ‘closed’ on shutdown sets the modified time. It’s hard to say for 100% sure and to be honest I have looked at this timestamp enough today 😉
Thank you all for your responses and help, especially Joe and Brian, but also all the nice people on Twitter and Chad Tilbury who responded to my emails despite his exceptionally busy schedule.