The USB forensics thread can continue until the end of time, or at least the end of my free space on here, with this in mind I am only showing you the basics of USB forensics. I may cover more depth in later posts, I may not. What I can tell you is if I do, I wont be using that bloody Seagate Hard Disk!!
For the final part of this puzzle we are going to visit a file not yet seen:
%WINDIR%\inf\setupapi.dev.log
This is very similar to the setupapi.log from Windows XP, except Microsoft moved it slightly further away. They have a habit of doing this I suspect its to charge more for consultancy or something.
Setupapi.dev.log can be viewed in a highly complex program known as Notepad, this program baffled many a developer by using a feature called “word wrap”. Seriously just turn it on and resize their window, then sit back and laugh!
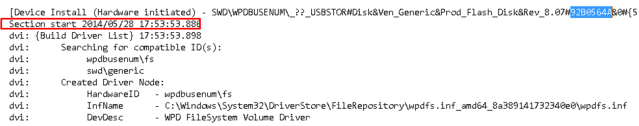
As you can see highlighted above is the Device Serial Number all the way back from Part 1. This is the string you will need to search for to find the device. The area in the red square is showing the time the device was first connected.
WARNING!! The time shown above is in the System local time not UTC!!
I was going to put that warning in red, but after the word wrap incident I don’t think the dev’s could handle it.
And typically the Seagate Hard Disk decided, like a petulant child, not to bother showing up in the log. I tried a search on the Serial Number, GUID, PID and VID. Nothing!
Last time device was connected
We know the first time the device was connected, now we need to know the last.
A change from Windows XP worth pointing out, this next step used to be how you found out the first time a device was connected, now it’s for the last time (from Vista upwards), I am sure Microsoft had their reasons and I strongly suspect word wrap was involved somehow.
Go to the following Key (again):
SYSTEM\CurrentContolSet\Enum\USB\VID###&PID###
If you are using Registry viewer you will see the last write time of this key. This is the last time the device was connected. It is also possible to confirm the last time a specific user used the device by going to:
NTUSER\Software\Microsoft\Windows\CurrentVersion\Explorer\MountPoints2\<GUID>
These times are in UTC not system local time. Timestamps are annoying and this is one of those times! I would recommend recording everything in UTC and annotating which were displayed in local system time. This helps with your time line.

Pingback: Can Windows Update fool you during the investigation? – CyberDefNerd