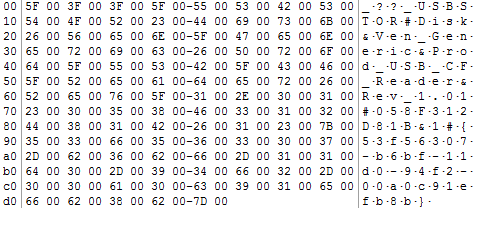
Here is a screen capture of a Mounted Devices key. As you can see it can appear quite daunting.
In a previous blog post I covered how a USB Mass Storage devices would simply convert ASCII to Hex and use that as the data field as seen here:
This explains the longer Hex strings starting 5F (_) and 5C (\). Now let’s look at the shorter strings….
When I carried out the USB Forensics research for my earlier blog posts I did not believe there was much use in the other Hex values from the first image. I know “C:” and “E:” are physical installed hard drives and “D:” is a CD ROM drive; leaving “F: G: H: I:” as removable devices.
You will notice that there is a distinct difference between F & G and H & I. Both drives H & I are USB “Pen Drives” and although look identical are actually two different devices with “Generic&Prod_USB” at the start of the description.
F & G however are seen as disk drives (one is actually an Android device, but I am not going to touch mobile forensics today 🙂 ). The G: drive is the elusive “My Drive” device from the USB Forensics series I did earlier in the year.
What does it all mean?
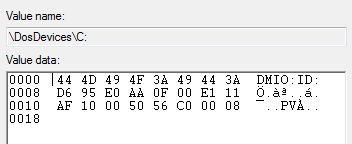
Let’s start with the C drive.
You can see from the ASCII translation this disk starts with “DMIO:ID”, this threw me a little during my initial research as both drives have the same information. I then realised this was because they are Dynamic Disks. I am not going to talk about using this key to identify Dynamic Disks as this is regarding removable devices and in my experience it is highly unlikely a Dynamic Disk would be used as removable storage due to the limitations of Operating System that would come with it.
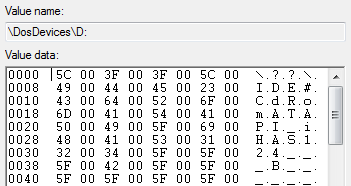
CD-ROM (DVD, showing my age)
As you can see from the ASCII this tells you it’s a CDROM drive. Simples.
Skip the USB Pen Drives as they are covered in the USB Forensic series
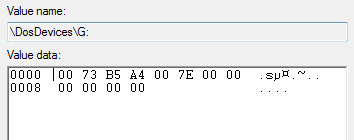
“My Drive”
Here we have the G: drive which is the USB HDD known as “My Drive”
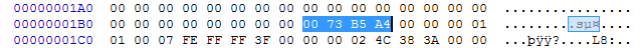
The first 4 pairs of Hex (00 73 B5 A4) are the important ones in terms of identifying the drive. These show the Disk Signature of the drive.
Using a program like HxD it is possible to open the drive up (other Hex editors are available) and so far I have always found the Disk Signature at 001b8-001bb
This disk signature will change if the disk is formatted. Therefore proving with a high degree of certainty that this is the device you are looking for. After all in order to get this number twice from the generated system would be 1:(16*16*16*16*16*16*16*16), so possible, but very unlikely.
The remaining Hex is related to offsets, if you search for “disk cloning” or “disk signature collisions” you will see many articles explaining the full breakdown.
How is this even useful?
Well from the USB Forensics series you will see that it was a little inconclusive in places and proving that the “My Drive” device was plugged and hadn’t been formatted since was difficult. Using this method you now at least have an alternative to the volume ID for slower non-readyboost devices.


The binary values – obviously Unicode strings – seem to be \GLOBAL?? object used in the NT object namespace (see Windows Internals book). However, this paths when disregarding the leading “\??\” part and replacing all “#”s with “\”s should yield valid sub-keys of HKLM\SYSTEM\CurrentControlSet\Enum.
The thing I don’t understand is the “DMIO:ID” references on my work PC because we’re not using dynamic disks, there are none! Could it be that GPT disks appear like dynamic disks in “\DosDevices\:” references?
Note: It should read “… \GLOBAL?? object *references* used …”, sorry!