There is some mis-information around; that encrypted traffic is useless, and you should go back to netflow and statistical analysis only. I disagree. I will be doing a few posts showing clear-text information leakage we can use to our advantage.
Let’s start with a biggy;
What site was visited?
Imagine you need to prove a user went to a specific website. Providing the site isn’t on the HSTS pre-load list within the browser, you can see this. (We will visit HSTS and the pre-load another time, but for this instance we will assume malware, or nefarious activity which wouldn’t be included in this list).
I am going to pick on the truly evil wikihow website (just because I used them in a HTTP-PCAP-CTF a few years back before they moved to HTTPS and now I am proud of them 🙂 )
So a user is suspected of faking their new job and visiting wikihow to see how to do stuff. We check the packet capture and run a filter looking for GET requests to wikihow.com. We don’t see any…. then the IT dept tells you SSL breakout broke a while back, and the CEO dictated it was turned off as it was stopping him streaming…. work…. stuff.
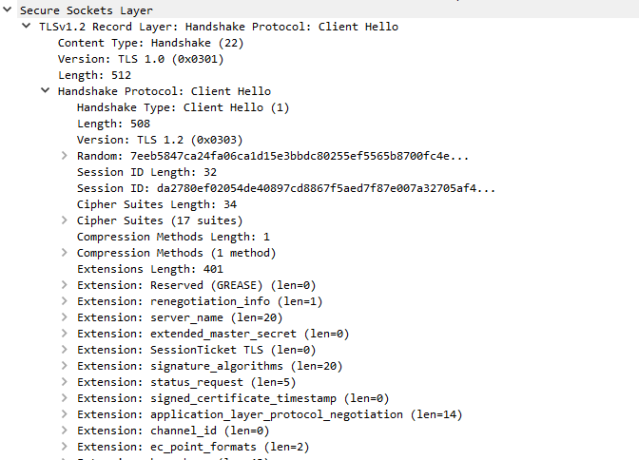
Now we have an issue. We filter this users machine, pull the packets only for the time frame this person was suspected of the activity (cutting many corners for ease here, just go with it). We find lots of SSL Handshakes and have a closer look…..
Easy right?
Kidding 🙂 The answer is actually under “Extension: server_name”, but there is an easier way. Follow stream!
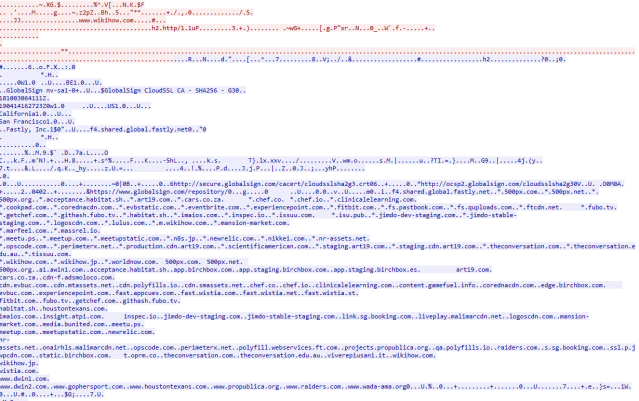
The orange coloured part is outbound from my PC, the blue part is the response. You can see here “www.wikihow.com” in the packets.
We can also see something interesting in the response. This is a shared certificate and all of the sites listed share this certificate. I am not going to cover certificates, as this would need me to talk about key exchanges which hurts my head. Just accept that certificates can be shared and data is still secure… ok? cool. If you want to know more, there are lots of really interesting sites on the subject.
Why do I care?
This information can help with an investigation while you are waiting for someone to bring you the private key, or if no keys are available. You can at least check all of the requested sites. This would be the encrypted equivalent of looking at all GET requests (kind of… all GETs would also show resources within sites, this won’t… but you get what I mean).
If you want to look for all ‘Client Hello’ requests in a PCAP use the following Display Filter
ssl.handshake.type == 1
Red Team Recon
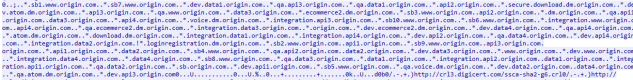
This is a nice easy way for pentesters to recon a site with normal user behaviour. Looking at the response to the Origin API (see last paragraph) I can now see lots of sub-domains to play with:
What information does your certificate leak about your company?
Side note
This can be interesting to see what your machine is doing, while I was running this capture I also unintentionally captured a request going to api1.origin.com. I have the origin client installed, but it wasn’t running at the time. Now I know that Origin has a service that runs in the background doing something…..