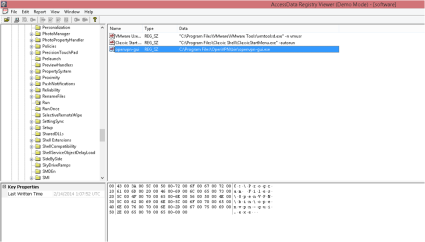
Windows Registry keys keep a time stamp embedded within them. This cannot easily be seen using regedit.exe, so instead we turn to our trusty Forensic tool kit.
First off I used FTK Imager to capture locked files. This allowed the Hives to be copied and saved into another folder. From there I opened Registry Viewer (both products are made by Access Data, the links are supposed to be the same 🙂 ) and accessed one of the offline Hives saved to the location I specified earlier.
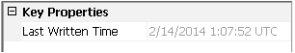
From the screenshot above you can see the Registry viewer is not too dissimilar from regedit.exe. The important part for this post is in the bottom left hand corner. Let me magnify it for you…..
As you can see this was last written to on the 14th Feb 2014 at 01:07am UTC. It is important to know if you are running in UTC or local time as this can cause huge confusion. Running your Forensics VM in UTC is usually helpful. I will show you in a later post how to see what time zone the imaged machine was running in, as well as if DST is active.
With the registry time stamp it is important to remember that it will only show the last time it was written to, it cannot be used alone to create a time line, this will need other artefacts (which will also be covered in later posts).