What is a Jump List?
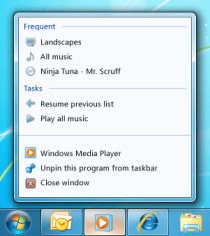
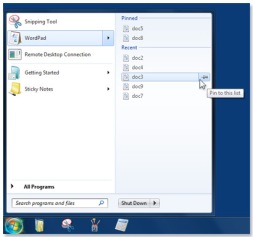
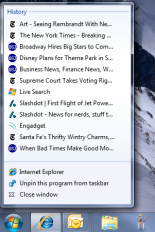
A Jump List looks something like:
From left to right we have;
- Windows Media Player
- Start Menu, Wordpad
- Internet Explorer
Jump Lists were introduced in Windows 7 to allow frequently used files/tasks/webpages to be selected before opening the file. This can be anything from a recent Wordpad file to setting yourself to invisible on Skype.
By default applications have the following Jump List options available:
- Launch the application
- Pin to taskbar
- Close all currently open windows
Each jump list is split into “Destinations” and “Tasks”. Destinations are the upper part of the Jump List and will include recently opened files or website history. The Tasks are the lower part of the Jump List and may contain frequently used commands.
Where are Jump Lists Stored?
Woah! Steady on there Billy, first off we need to discuss Application ID’s (AppID). These are universally unique identifiers for each application. Of which there are quite a few
http://forensicswiki.org/wiki/List_of_Jump_List_IDs
Here are a couple of examples from the Forensics Wiki
- 32bit Outlook – be71009ff8bb02a2
- 32bit Powerpoint 2010 – 9c7cc110ff56d1bd
- Truecrypt v7 – 17d3eb086439f0d7
- 64bit WinRAR – 290532160612e07
The location of the Jump Lists is split into two locations
- C:\Users\<user>\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations
- This list is created by the O/S and not the application
- C:\Users\<user>\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations
- This holds all of the information the application has created and would need testing and verification of each application to prove the data held here says what you think it says!
The Automatic Destinations folder is a good place to start as the parameters of the data held in there will be the same as the automatic Destinations folder on another machine of the same operating system.
Automatic Destinations
What can we learn from this folder? Well for starters, when the program was first run. Use the AppID to track down the program in question and read the creation date. Simples.
The files themselves are a little less simple, they are stored using Structured Storage Format and need forensic tools to read them. For this we shall use MiTec’s Structured Storage Viewer.
I used this on my profile, attempted to find AppID f01b4d95cf55d32a and found nothing. After reading through the MiTec program I realised that it had my Documents, Pictures, Music and Videos on there as well as another random folder. The only icon on my task bar which contains those five locations was File Explorer. I confirmed this by browsing to another folder, re-opening the file and noting the new folder location had been appended to the file and was also visible on my Jump List for File Explorer!
The output from Structured Storage Viewer is not perfect (not the fault of the program, it’s not designed for looking at Jump Lists) but it allows you to view the Hex of the file and look for clues.
Custom Destinations
The files in this folder need to be viewed with a Hex Editor, the MiTec program will not open them. The contents of these folders can vary from virtually nothing to file paths which may indicate the nature of program.
Why use Jump Lists at all?
When dealing with a forensic investigation it is often best to imagine yourself standing in a court room explaining how you came to that conclusion with someone of greater experience rebutting you. A lot of artefacts leave possibilities open. By proving the same thing from multiple angles you are removing doubt from the mind of the jury. Rather than thinking you are putting a guilty person into jail, think instead that you are trying to keep an innocent person out of jail.
Jump Lists can confirm that programs were run or files existed (or at least a file with that name) on that machine at some point in the past. Jump Lists are also not the type of place anti-forensic tools may look. With the modern registry hive data is stored in multitudes of locations whether in complete evidence or in fragments which need to be pieced together.
Add Jump Lists to your forensic locations and you will not be disappointed!