Part 3 of our investigation is to discover what the Volume Name of the USB device was. This can be helpful when looking into Link (.lnk) files (which I will cover in a later blog post). It can also occasionally go as supporting evidence if the user has named the volume after their own name, or better yet something telling like “Hacking Tools”.
Windows 7 upwards introduced a new key to the Registry which makes finding the Volume Name a lot easier than previous versions. Navigate to the following location:
SOFTWARE\Microsoft\Windows Portable Devices\Devices
This key is not particularly user friendly, in terms of readability, there are worse ones out there though! The Serial Number as identified in Part 1 will be the string you are searching for.
As you can see above the Unique Serial Number is displayed in the red box.
And this shows us the Volume Name of the USB stick from SANS named “FOR408-USB”
Before we continue……
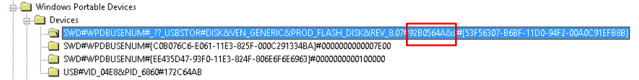
Something I noticed while looking at these keys, the highlighted key is not the device I wanted to demonstrate, the one I wanted to show is below it it. The second key however does not have the Serial Number in the key name. So how can we prove this is the same device?
I went back to the USBSTOR key for a little more information, after all this key was created as a result of the installation of the USB device the same as in the USBSTOR. Therefore logically there must be a way to correlate one to the other. So I started looking at the other characters in the key.
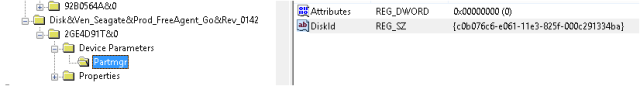
The “SWD#SPDBUSENUM#” is repeated on the third key, which is not the same device, therefore I discounted this from this investigation. I next looked at the bracketed string starting “{C0B076c6….. ” and discovered it is a reference to a value held under
SYSTEM\CurrentControlSet\Enum\USBSTOR\<Device>\<SerialNumber>\Device Parameters\Partmgr
Under “DiskId” as highlighted on the right, you can see the corresponding string (this is not true of the other USB device however).
![]()
Using this correlation, albeit a weak one, you can see that the Volume Name is set to “My Drive”, which is the correct device.
Conclusion?
I cannot explain why this is like it is, my only working theory is because the “My Drive” device is an external cylindrical hard drive, where as the first device “FOR408-USB” (with the Serial Number) is a USB Stick. Occasionally Windows struggles to differentiate between external hard drives and internal hard drives, the “My Drive” device is around five years old now, and only used for backups, I may try this again in the future on a modern drive and see how that plays out.
Thoughts
My thoughts on this are that as a forensicator we need to be dynamic and have the ability to adapt. While the above process is open to debate, it is a smaller part of a bigger picture. If we can find other evidence to reinforce this then convincing a jury becomes a little easier. I find it unlikely this would be the only evidence to be brought forward in court case, and to quote (paraphrase maybe) Chad Tilbury “make a note of it and move on”.
This once again brings us back to note taking. If in your notes you can explain why you did what you did, and another forensicator would come to the same conclusion after following your process, then it is justifiable. Windows is not designed with forensics in mind, this is both good and bad, it helps make anti-forensics difficult, but by the exact same process it makes forensics difficult….. and fun 🙂
As always comments on this subject are welcome, this is a learning blog and I believe constructive comments are a critical part of learning for us all.

This is fantastic – thanks so much! I have been searching for a way to attribute devices with volume names and link files and I think this is exactly what I need. Thanks again!
Pingback: SANS CDI Forensic Challenge!!! | digitalf0rensics