Click here to view this research on my YouTube channel
What is AnyDesk?
AnyDesk is a legitimate, non-malicious piece of software that is used by companies world wide to manage their IT systems, and can be used for free to help family members with IT issues.
It is the scammer’s tool of choice because it is very easy to download and set up. There are also several options within AnyDesk that will allow the attacker to lock the victim out of their own machine, giving complete control to the attacker.
AnyDesk have taken steps to present the victim with alerts, and even disallow certain actions by the remote device, but the scammers utilise social engineering techniques to bypass these easily.
AnyDesk can be downloaded from the AnyDesk website here
Technical Aspects
AnyDesk can be run in two ways; installed like a tradition piece of software, or as a portable executable (PE). The way the software is run, will dictate the artefact locations on the disk. However the artefacts discussed here will be the same in both locations.
PE
C:\Users\<username>\Appdata\Roaming\AnyDesk\
Installed
C:\ProgramData\AnyDesk\
To check which way this application is being run, look at the file properties of the AnyDesk application. If this is from a scammer, it is most likely going to be in the Downloads folder, or the Desktop.
GCAPI.DLL
GCAPI.DLL is required for AnyDesk to run and for PE version may be seen in the same location as the executable, or will be seen in the Temp folder.
For user temp (PE) you will be looking by default in
c:\users\<username>\appdata\local\temp
For system temp (installed) files you will be looking
c:\windows\temp
AnyDesk will search for this file and download it if it is not already present. Later versions uses hash check due to search order DLL vulnerabilities, which will be covered later.
Connection_trace.txt
The Connection_trace.txt file shows incoming requests with a status of
- User – for the local user accepting the request
- Passwd – a password being entered by the remote system
- Token – a ‘remember password’ check box being checked by the remote system
- REJECTED – if the local user has rejected the request
The ‘Passwd’ and ‘Token’ settings are only relevant if the local system has set a password for unattended access. It is important to note that this is for incoming requests only, and does not display any outgoing connection data.
This provides you with time stamps and IDs to help focus your investigation and give you that initial hook that the baseline of a DFIR investigation. Below is an example that I have redacted to stop you all trying to connect to my lab!

User.conf
The user.conf file is useful if an attacker has attempted to transfer files. You will get to see a directory path which, by default, will give away the username.
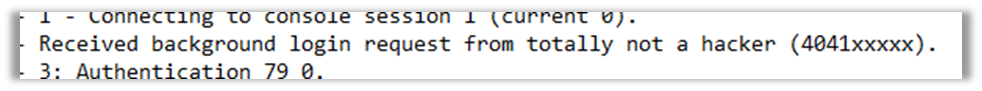
The connection from this host was ‘totally not a hacker’ which we can see is an alias for the local admin account.
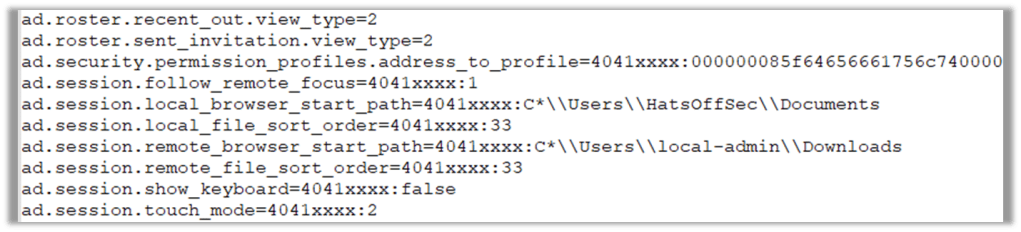
This tells us a couple of things, for one the account ‘local-admin’ is not created by Windows, which means this account was intentionally created with that name, and based off the name is most likely a local account and not part of a domain.
It also shows that the attacker is running (most likely) as an administrator on that host. This type of information helps to build a bigger picture, and when law enforcement are involved these small pieces of evidence help them to prove that this system was the one the attacker used.
Ad.Trace
The ad.trace file is a verbose log and will be where the majority of effort will be spent. Use the timestamps and IDs from the Connection_Trace file to focus your investigation.
If this host was a scamming victim that has never used AnyDesk before, this file will still be heavily populated, but at least the investigation will be simpler.
So what can we see in this file?
Well straight off the bat we can see the version of AnyDesk that is installed. This can be important if the attacker is intentionally using an old version. We can also see the version of Windows used by the victim. Which is more useful if the host is not available to the forensicator. Finally on this screenshot we also can confirm that AnyDesk was not installed when it was run.
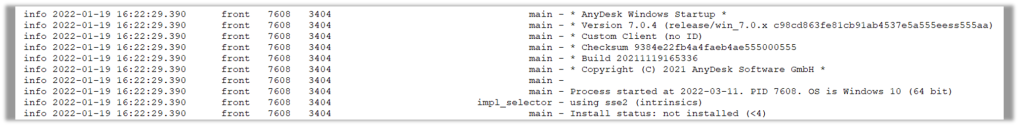
When looking at the version of AnyDesk the victim was running, we need to ask; why use that version?
Maybe it has features that don’t exist later? Maybe there are security vulnerabilities they can exploit? AnyDesk has worked to make the attackers life more difficult by adding features to highlight scam connections and disabling certain features. If an older version is being used, maybe it pre-dates these features.
Next up we look for the ID we picked up in the Connection trace file that was active at the time we need to investigate
First up 40410xxxx, which has been redacted for privacy (I don’t want you connecting to me… sorry.)

As previously seen, the alias of this is ‘totally not a hacker’, this alias field is typically the same as the local username, meaning this person has knowledge of the tool and what information is presented to the victim. While this alias is obviously done in jest, it could easily be ‘Microsoft Support’ or whichever agency the attacker is attempting to pass themselves off as.
This also shows us the remote version of AnyDesk and the Operating System in use
When setting this up I created an external AnyDesk system, rather than simply being on my own LAN, this was because I could see references to my own public IP address, but couldn’t prove if this was an artefact of the victim or attacker.

This screenshot shows the external IP address of the attacker, meaning we are able show where they connected from.
Obviously the attacker could take steps to use a remote proxy device or a VPN, but this is still another artefact to add to the collection that we are building around this user. If this is not their IP, could the IP owner be contacted? Are they aware that their systems are being used in this way? Do they keep logs?
Ad_Svc.Trace
As the attacker in this scenario forced a reboot of the remote machine, we are presented with a new artefact, the ad_scv.trace file. Typically you would only expect to see this on an installed version of AnyDesk, because it is the log file for the AnyDesk service.
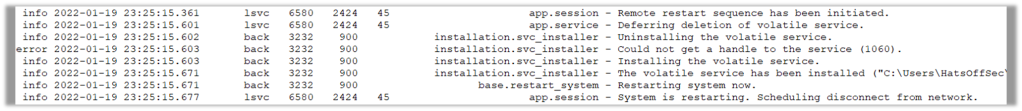
We are able to see that the restart was initiated remotely and the volatile service was created on the victim machine.
What does this mean? Simply means that the attacker set up unattended access on the victim machine and then restarted the host. This unattended access means the attacker can connect at anytime by using a password they set, or tricked the user into setting, on the host.
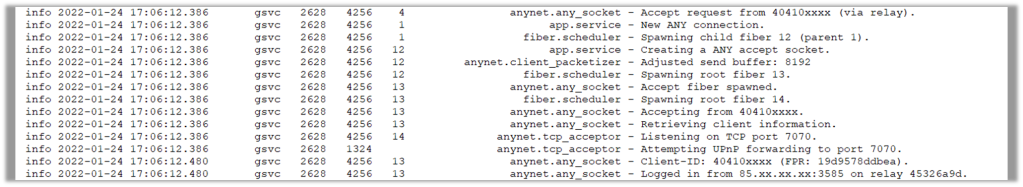
Next we see that the attacker reconnects with the same ID and same IP address. This could prove useful if the attackers are using a ‘speak to my manager/support/customer retentions’ method. It will show if that person is using the same host, or is using the same IP address as the initial connector. This may also prove useful if the victim reports unusual activity involving the mouse moving on its own, or other indicators someone has control of the host.
Chat
Anydesk has a built in chat feature which allows the remote and local user to communicate over text messages. The log of this file is held in a subfolder of the AnyDesk directory
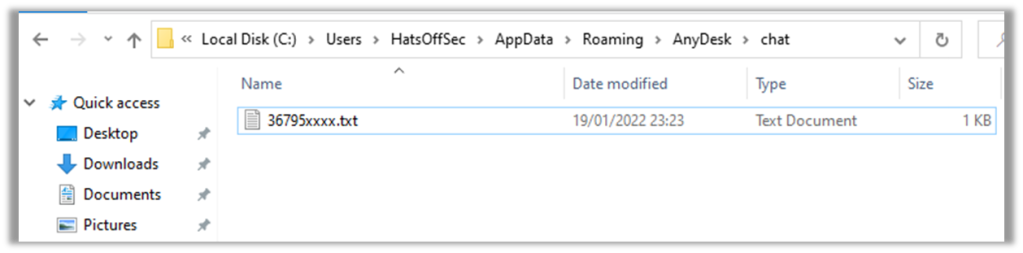
This will have a text file named as per the client ID of the connecting AnyDesk. In here will be both sides of any chat conversation that was had. This could be very useful if the attacker used that to communicate with the victim. However most scammers will use the telephone.
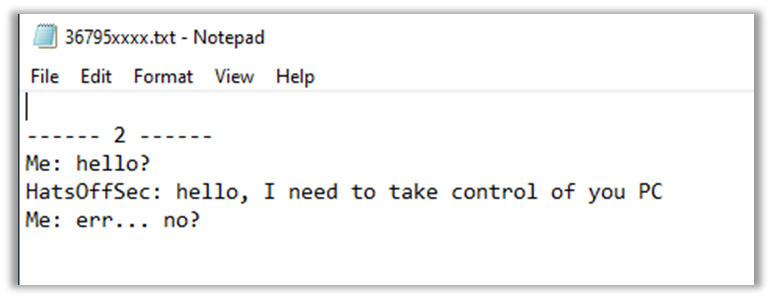
These chat logs may not be used too often by Scammers, but they may prove useful in other forensic investigations.
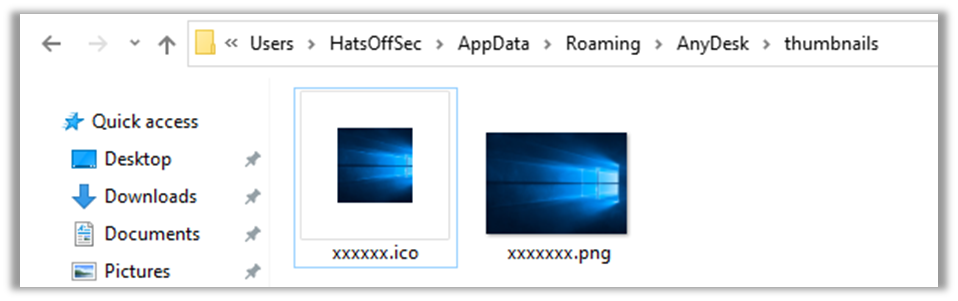
Thumbnails
Finally there is the Thumbnails folder, which keeps a small image of any machine connected to from this AnyDesk session, typically this will show the wallpaper in use by that machine, however is only available when an outgoing session has been established.
This would prove most useful to the law enforcement agencies whose job it is to prove the machine they are investigating is the one responsible for the connections.
Vulnerabilities
Earlier in the post we talked about using a specific version of AnyDesk and what that may mean.
There have been several vulnerabilities relating to the product, but mostly these would not be of interest to a scammer. Instead these are more interesting if you see old versions of AnyDesk downloaded as part of a malware campaign, or an attack. Especially if the GCAPI.dll file is provided as well.
Below are a list of CVEs relating to older versions of AnyDesk that could be exploited. The local privilege escalation in CVE-2021-40854 is trivial, but requires GUI access to the chat logs. the tl;dr is that you open the chat logs in a SYSTEM level notepad by default, then use File > Open to run cmd.exe.
CVE-2020-13160
AnyDesk before 5.5.3 on Linux and FreeBSD has a format string vulnerability that can be exploited for remote code execution.
CVE-2020-27614
AnyDesk for macOS versions 6.0.2 and older have a vulnerability in the XPC interface that does not properly validate client requests and allows local privilege escalation.
CVE-2020-35483
AnyDesk for Windows is vulnerable to a DLL hijacking attack, where an attacker places a malicious “gcapi.dll” file in the application directory and then sets the read-only attribute to prevent the file from being overwritten. AnyDesk will then attempt to load this DLL file when executed.
If an attacker can place a “gcapi.dll” file in the application directory, AnyDesk will run any malicious code contained in that file. The code will run with normal user privileges, unless the user specifically runs AnyDesk as administrator.
Note: this is especially critical for the portable version of AnyDesk, which is likely to be started from an unprotected non-system directory like the browsers download directory.
The vulnerability affects AnyDesk for Windows from versions 5.4.2 to 6.0.8.
CVE-2021-40854
AnyDesk before 6.2.6 and 6.3.x before 6.3.3 allows a local user to obtain administrator privileges by using the Open Chat Log feature to launch a privileged Notepad process that can launch other applications.
CVE-2018-13102
AnyDesk before “12.06.2018 – 4.1.3” on Windows 7 SP1 has a DLL preloading vulnerability.
CVE-2017-14397
AnyDesk prior to 3.6.1 on Windows has a DLL injection vulnerability.
AnyDesk Advice
https://support.anydesk.com/knowledge/abuse-management
AnyDesk offer advice to users, however the sad truth is that most home users who would be scammed have probably never even heard of AnyDesk before they are scammed out of their money. As such it is the job of people like you, reading this blog post, to help ensure that when this does happen. We can provide as much detail to law enforcement as possible to help them catch the scumbags behind this.

Pingback: Week 10 – 2022 – This Week In 4n6
And if the scammer using a VPN you think that anydesk gonna know his real ip address in order to identify the user ?
Hey Alex, let’s break this down. If the attacker is using a VPN, and *if* the provider is keeping logs, then law enforcement will use the data we talk about here to identify the account holder.
If they don’t keep logs they *should* be on an grey list with AnyDesk and the user *should* get a spam warning (I am saying should as this is not documented for obvious reasons).
If the VPN is a privately created one, law enforcement can work with the host provider (Azure, AWS etc) to get logs of who owns the account that created the VPN endpoint.
Another question would be what happens if this is a TOR exit node IP address, and for this I would hope that AnyDesk flag it, or block it from establishing a connection.
With any investigation there is a risk that the attacker has taken steps to protect their identity, but eventually they will make a mistake. By capturing the data, law enforcement can compare that with other attacks to see patterns. Then simply wait for the attacker to make that inevitable mistake.
After all, Lulzsec was historically compromised after one of the members allegedly forgot to use their VPN one single time when logging into a forum. All it takes is one non-VPN connection and law enforcement would be able connect all of the scammers activities.
So while you have a valid point that a single investigation into a single connection may not give the real IP address, it is still important to carry out these investigations to the best of our ability to pick up all of the information that we can. It may be that your investigation is the one where the attacker made that OpSec mistake and you are the one the law enforcement agencies have been hoping will do a thorough job.
It have been a while since we talked about this issue with anydesk and if they can trace scammers who using VPN from there and I have a question which is:
Can anydesk trace the scammer even if he using VPN due to it’s installation on the scammers computer too?
Because as far as I know when an app or a programm is installed on a device, it can be tracked down even with multiple VPN’s because they can identify the device ID therefore the user who owns it.