I thought I would write about my experiences with the Christmas Hacking Challenge by SANS, I am writing this before Christmas, but I wont publish it until after the closing date for obvious reasons 🙂
The challenge has an amazing adaptation of a Christmas Carol by Charles Dickens. It explains how Scrooge’s old server Marley, who was dead to begin with, came back to life to pass a message on to Scrooge; hack for good. Excellent read, very entertaining and well written by Ed Skoudis and his team.
Questions
There are 3 questions which challenge you to find 7 flags.
Q1. What message is left at IP address 173.255.233.59 (1 flag)
Q2. What secrets are left on the site http://www.scrooge-and-marley.com (2 flags)
Q3. What secrets are left on the USB Image provided to Scrooge (4 flags)
Answers
As I have said before this is a learning blog, learning for me and hopefully something for you guys too. As such I am going to take you through my thought processes for the answers.
Another quick note, I am a Windows geek. My background is as a sysadmin and IT support work, I was only introduced to Linux recently. In fact while doing a SANS Netwars event a few years back James Lyne was moderating and I asked for clarification on a level 1 question. It was something nice and easy that required you to look in a user’s mailbox and copy/paste part of the message. Quick win I thought, but I see no mail client on this image…..
“James! About this question, it is asking me to look at an email, but I can’t find a mail client?”
“Well, what is a common mail client in Linux?”
“…………………………….Outlook?”
“……………no………”
While my answer was deliberately facetious, it proved to me that I didn’t even have a basic grasp of Linux. It has been a few years since that event, and I have been learning ever since. The reason I tell this story is to explain why I will often use Windows tools when there is a Linux option, and also why I may appear to go the long way around things. Any feedback on faster ways would be appreciated 🙂 This will also be important in answering question 2.
Question 1.
For me this was much more difficult than it really should have been. However hindsight is a wonderful thing!
To start off with all you have is an IP address, it is far too easy to forget there are high numbered ports and I know a lot of people (me included) started off with thinking this was an SSH challenge. It wasn’t.
Port 31124 was open and had an Eliza chat bot running on it. You can connect to this port with telnet and speak with Eliza. She refuses to tell you her secret, claiming that someone may be shoulder surfing you. Some people tried to brute-force the chat bot thinking there was a way to get Eliza to tell you the secret. The answer was far simpler, but wasn’t something I wanted to give. My own IP address!
First; the process. I used PuTTy to connect to port 31124 and got this prompt (it looks prettier in Linux)

After asking her 3 times for her secret (you can literally type “secret” and get the same result) you get to this impasse.

The correct instruction to get Eliza to visit a webpage is “surf to http:// <url> ”
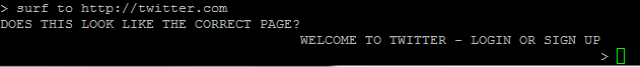
Now all you need to do is get her to communicate with something you have control of. Ed Skoudis gave a hint in one of his tweets.

Direct her to you, or a place you can read her requests. I decided to go against my inner-paranoid self and open up port 80 on my router and allow her to browse to it (I have port mirroring and full packet capture already set up, this would’ve been a lot harder with an ISP router).
I fired up Wireshark, disabled my any-any-deny rule on my firewall (I could’ve added allow port 80, but I calculated the risk of no deny rule for 30 seconds as acceptable) and did a live capture with the following wireshark filter
ip.addr==173.255.233.59
I then typed “surf to http:// <my ip> ” into eliza and watched as she sent a get request to my router.

Apologies for the terrible redaction techniques, I am not a graphics designer, so I used the snippet program to do it 🙂
As you can see in Eliza’s “User-Agent” field, we have her secret!
That should’ve taken around than 30 minutes, maybe an hour with interruptions, but as I said hindsight is a wonderful thing! That took me a lot longer.
Eliza Secret: Machines take me by surprise with great frequency -Alan Turing
Question 2.
On the SANS website we are given permission to attack scrooge-and-marley.com on ports 80 and 443 only (and I assume only for the duration of the competition, so check before testing anything I am about to talk about).
I figured the SANS guys would want to be topical and look at vulnerabilities that have come out this year. Shellshock and Heartbleed being the two biggies.
I realised that www. scrooge-and-marley .com resolved to http://www.scrooge-and-marley.com and not https. I thought it odd to have both in a competition for no reason, also we were given permission to attack 443 as well as 80, basically this was screaming Heartbleed at me. At this point I could’ve proven my metasploit ninja skills (of which I have none) or I could turn to Google.
One of the first hits was this site which had a scanner! yay! So I put in the URL

And the site was vulnerable. Excellent.
As you scroll down through the embedded window you can see a Dickens-esque passage followed by “Secret%20%231” which when you convert the encoding back to ASCII comes out as “Secret #1” with the full flag reading “Secret #1 Hacking can be noble”

While I am sure there was a Metasploit plugin for this I was happy to connect to this site via VPN and use it as a pivot point to attack the site (I used the VPN out of good practice rather that genuinely trying to mask my tracks).
Website Secret #1 Hacking can be noble
On to the next secret!
The problem is, that was the easy part. Heartbleed takes a specific command and returns a specific result (as I understand it), as such using an automated tool like this makes for an easy win with little skill involved. Secret #2 on the other hand, is being a stubborn pain in the ****
Shellshock! Is the site vulnerable? According to almost every scanner I used, no it’s not. as I was playing around with Burp suite and scanning the site I noticed a hyperlink at the bottom of the page which leads to a contact page. Within here there is a form to fill out. I was hoping there would be a SQL injection part to play, as these are well researched and all over the web; this was also the reason I thought it probably wont be that!
I looked at the page source and noticed a reference to a “submit.sh” file, I am not a web-dev, but I thought it was odd to have a .sh file under the submit button. Research then ensued.
Shellshock Research Time
My first job was to learn how Shellshock works with websites, I have seen a few articles and done some basic research around this, but as it hasn’t come up in an engagement thus far, I haven’t done in depth learning.
One of the first pages I visited was a blog post by John Graham-Cumming of Cloudflare. This was the first good post which actually explained in practical terms how Shellshock worked. John also explains how to incorporate Shellshock into Curl and HTTP headers.
Using the Curl script John described would not provide me any feedback from the site, I needed a flag to be delivered to my screen and although ejecting the CD Drive amused me, it probably wouldn’t work anyway. So I started on the HTTP Headers. Burp suite loaded and ready to go!
Attack #1
After reading John’s article I decided to “inject” my code into the User-Agent: field. I simply deleted the “Mozilla/5.0…. etc” that was in there and replaced it with

I realised as I put this in that there was no way the server could respond to me, I was sending it a command which would be output…. where? Certainly not printed nicely to the webpage. I declared victory and moved on. The next train of thought was to get the server to email me the answer, this was also explored in Johns blog post.

I honestly didn’t expect this to work…. and I was right. This relied upon a mail client/server being installed, and allowed on the victims machine, and that just didn’t seem right. Oddly enough no mail arrived in the email address I entered (obviously that’s not the actual email address I entered)
At this stage I was starting to think that intercepting the headers wasn’t going to provide a win. From what I could tell, this was used to compromise machines or to provide recon via pinging.
Attack #2
Next I used wget to pull the submit.sh file and it worked as expected. Then I remembered John’s post had a curl command, so I attempted a wget with that command instead. After I realised donwloading files was annoying I switched to curl, so let’s gloss over wget and talk about curl.
Curl needs the -H switch (Header). My initial results kept coming back with “500 Internal Server Error” which was kind of annoying.
After a little more research I found this question and answer session on stackexchange.com. The main answer explained that adding ‘echo; echo’ to the command avoids the internal server error. Now things started to take off!
Quick disclaimer, yes I am logged in as root, this is a non-persistent VM which I have used for this blog post! Also SIFT Workstation, free plug. This does show however, you don’t need to use Kali or Backtrack for this part of the challenge. I did use Kali earlier for Question 1. However I did not write this blog post in that order 🙂
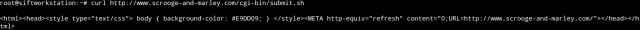
This is a standard Curl command, nothing special, I just wanted to show you what the script looks like without any additions.
Next I added the Shellshock script with a simple test of echoing “Hello World”

At this point I was happy that I had gotten a result which was different from the norm. I now need to test other commands….
This actually was very frustrating, I could not get any other command to work, except one

PWD (Present Working Directory) shows /var/www/cgi-bin. At this point I was starting to get a little excited, I have now managed to get the server to tell me a little secret (sadly not the secret I want) meaning that I have used Shellshock correctly and executed some code! I admit I got a lot of help, but this is still a big win for me personally.
Now what though?
I realised from PWD that there is a whole directory structure beneath me, I stumbled across the idea that “echo *” works similar to ls

I kept the PWD command in as a confidence check (as when a command fails you get a blank page). “echo *” had provided me with the contents of that directory. Win! Now what?

Directory Traversal that’s what! Feeling like a proper hacker now mum!! (my mum doesn’t read this).
Here you can see the pictures from the initial web page, the contact page and the index.html! Also the a.ogg file with James Lyne providing young American women something to keep them warm at night.
Let’s not stop at one lot of dot dot slashes!

At this point I wanted to run and grab my wife to show her what I’d found, upon realising that 1. She was in bed, 2. She wouldn’t understand and 3. She would explain to me in very few words just how little of a s**t she gave. I decided not to. Instead I decided to continue.
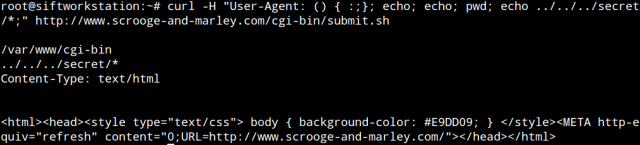
It was at this point my joy turned into perpetual frustration. I have managed to find the folder = win. I have not managed to see if there are any files in there, or get to the files! I have tried adding /bin/bash/cat or /bin/bash/ls I have tried piping cat to echo I even tried echo $(something) which just ended in confusion.
I have to admit at this point I got a little tip off; perhaps the ../../../../secret is not a folder. I was also advised to read the SANS blog posts.
A blog on reading files within a restricted shell!? Wow that sounds familar!!
At this point I should have gotten the answer pretty quickly, but as I said earlier, my Linux skills are not as high as I would like them to be!
The blog post gave two instructions; one of which I was really pleased to have figured out all by myself!
That second one looks perfect! That’s what I need!
Some of you may have already figured out where I was about to go wrong.

I used “echo start” and “echo stop” to prove the script hadn’t failed mid way through.
This confused the hell out of me for a while, I sent the command to a buddy who pointed out that by not escaping the special characters, they were being run locally! I would like to say I said “oh of course”, but in actual fact I just said “oh, really?”.
So I updated the command to say

By adding a single character, the command now works!
Website Secret #2: Use your skills for good.
Question 3.
The USB image! All we are told is that there are 4 secrets on this USB image, sounds simple!
Luckily I have recently gotten X-Ways forensics through my company, this made life a little less painful. Also with my job being heavily involved in forensics I should have no excuses on this one!! We will see 🙂
When you first open the image you can see a three distinct files:
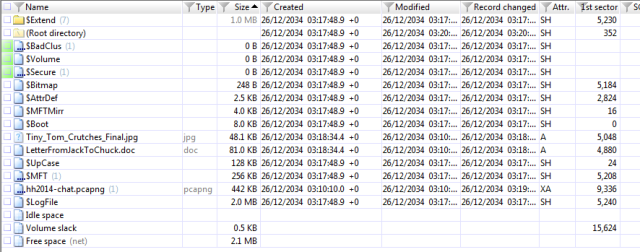
Tiny_Tom_Crutches_Final.jpg, LetterFromJackToChuck.doc and hh2014-chat.pcapng.
I will start with the Word Document. Why? Because I know that is where Secret #1 is obviously 🙂
Firstly I read the file within the X-Ways viewer, then extracted it to a VM where I would carry out an in-depth and complex investigation. I started by right clicking the file and going to properties. I noticed a “custom” tab which is a little unusual, so I clicked it.

Well, that was easy.
You could’ve also used exiftool to get this data, I actually prefer doing it that way most of the time.
USB Secret #1 Your demise is a source of mirth.
Next we will look at the PCAP file, this was actually incredibly simple, providing you know what you are looking for (duh). I did not know what I was looking for, so this drove me nuts for a long time. I was convinced there was something in the packet data.
Eventually I looked at the differences between a pcap and a pcapng. There are a few differences, one of them is comments.
In Wireshark there is the option to view comments under Analyze > Expert Info

Which gives the following box

That looks suspiciously like Base64 on the top line! (the second line becomes important for a later secret)
Lets go and decode that string.

tadaaaa

USB Secret #2: Your demise is a source of relief.
Now for the next secret X-Ways actually saved me a lot of time, there is a .zip file ‘within’ the PCAP, X-Ways just trivially popped that out for me. It’s not actually in the pcapng file (the zip file is 1.4MB, the pcapng is 404KB). X-Ways makes it look like a sub-directory of the pcapng file.
Bed_Curtains.zip containing Bed_Curtains.png.

Balls.
Anyone fancy a brute force? No? Me neither. So let’s have a think…..
I remembered something that stuck out on the website (you did read the whole thing, right?!)

The capitalization of the word Cewl seemed a little convenient. So I did some hardcore in-depth and vigorous research (yeah I Googled it).
The top result was a word list generator from websites (think ‘strings’ on a webpage). I knew there was a reason I follow Robin on Twitter 🙂
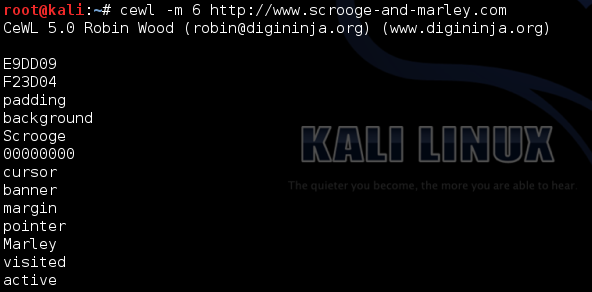
The -m 6 switch limits the results to words of 6 characters or more. The reason I did this is slightly cheating, I realised the SANS guys would want to prevent trivial brute force attempts therefore I would not expect a password under 6 characters. More likely 8 or more characters.
Thanks to Robin’s tool we now have a dictionary list 🙂
Believe it or not, I never actually used a dictionary attack, I got the correct password first time by guessing…. no really, I did! I looked through the list for a word I would choose as a password and “shambolic” jumped out as an amusing and fitting password.
Remember I said I liked exiftool?
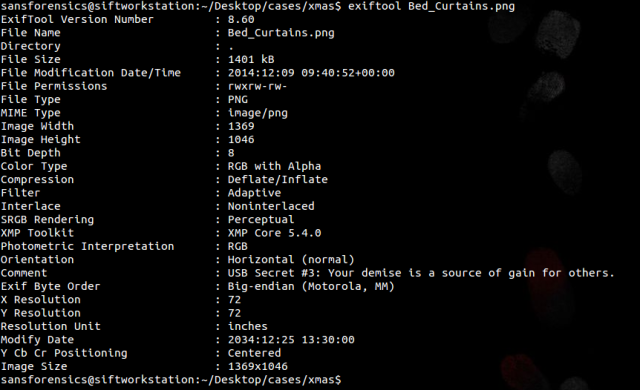
As you can see in the “comment” field we have our 3rd secret!
Secret #3 Your demise is a source of gain for others.
Final secret!
Tiny_Tom_Crutches.jpg is the only file out of the original list we haven’t looked at. First step, extract it. As this was the only jpg I was convinced it would be something in the meta-data!

Damnit.
Waaait just a second, what is that comment? jpg’s don’t usually have that comment in them…. do they?
Copy/Paste > Google. Second hit talks about Steganography! That sounds like something evil the SANS guys would do!
Hang on, wasn’t there something in Wireshark that mentioned Steg?

Yup. That was result #2 in Google. Something seems to be adding up here.
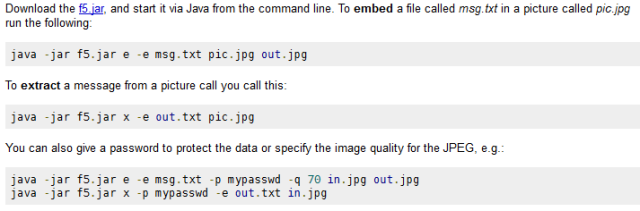
Oh what’s that, you have detailed instructions explaining exactly how to do this? Hmmmm… best give that a shot then.
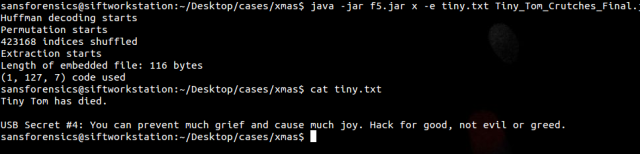
BOOOM Headshot!

USB Secret #4: You can prevent much grief and cause much joy. Hack for good, not for evil or greed.
All secrets.
- Eliza Secret: Machines take me by surprise with great frequency -Alan Turing
- Website Secret #1 Hacking can be noble
- Website Secret #2: Use your skills for good
- USB Secret #1 Your demise is a source of mirth
- USB Secret #2: Your demise is a source of relief
- USB Secret #3 Your demise is a source of gain for others
- USB Secret #4: You can prevent much grief and cause much joy. Hack for good, not for evil or greed.
Conclusion
Despite the way I may have trivially summarised the results in the post above, this was not an easy competition. Obviously the last four where a lot easier than the first three for me (the pcapng one was the last one for me to get). I would love to say I did this with no help at all, but there were some very kind people offering out tips. Never answers, only pointers.

I am very happy with the whole exercise, when I started this I had a very limited understanding of Shellshock and just how dangerous it could be. I had also never used directory traversal or any of the other commands in an attack/pentest. There were many moments when I thought I would never get all of the answers. I then asked the community for help and got some excellent advice, proving to me that we have an excellent community of people willing to help each other.
This blog post was written in multiple parts ranging before Christams to the 3rd Jan. So if there are parts which appear dis-jointed I apologise, I always struggle proof reading my own stuff 🙂